一 : 在Windows7中将U盘用BitLocker加密的操作步骤
在本文我们再为大家介绍一个Win7系统的小应用,就是给你的U盘加密。U盘是我们经常使用的一种移动设备,现在大多的容量也到了8GB或者16GB, 以及更高,价格可以说非常便宜了。但是U盘保存重要文件,第一是U盘的丢失,第二是文件的私密性,都给我们带来一定隐患,以至于很大容量的U盘,我们不敢 放置特别重要的文件。其实,这很简单,加密不就行了吗?!没错,我们无需多花钱去买专业的指纹识别U盘,也不用购买专业的加密软件,只要使用Win7系统,就可以给你的U盘加密,一样能够起到保护的作用,这就是Win7系统里的BitLocker加密功能。
在Windows7中将U盘用BitLocker加密的操作很简单,你只需要在U盘所在盘符的右键菜单中选择“启用BitLocker”,就可以进入BitLocker加密向导。
建立加密U盘
首先是选择加锁方式,普通用户选择密码解锁方式就可以了,记得设置的密码须为强密码方式以杜绝暴力破解的可能。而智能卡解锁方式只适用于拥有智能卡的用户。
(智能卡是一张含有计算机芯片的小型塑料卡。智能卡通常由大型公司的信息技术 (IT) 部门颁发。若要使用智能卡,您还需要一个智能卡读卡器,该设备安装或连接到计算机并能读取存储在智能卡上的信息。)
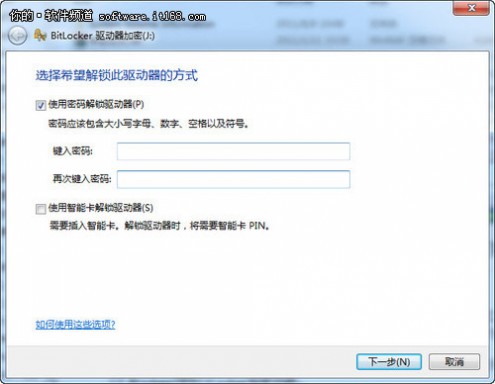
接下来是保存恢复密匙的选项,所谓恢复密匙,其实就是一个文本文件,里边是一串解密字符,在用户忘记密码时可以用这串字符来解密U盘,所以这个文件需要妥善的保管,如果你确认不会忘记你设置的加密密码,完全可以将恢复密匙删除。
(在计算机启动时,如果 BitLocker 检测到某个系统条件可能表示存在安全风险。如磁盘错误、对 BIOS 的更改或对任何启动文件的更改,则 BitLocker 将锁定驱动器并且需要使用特定的 BitLocker 恢复密码才能进行解锁。请确保在第一次打开 BitLocker 时创建此恢复密码;否则,您可能会永久失去对文件的访问权限。)

接下来就是一段时间的等待时间,等待U盘全盘的加密操作完成,所花费时间取决于U盘的大小及传输速率。别担心,就是这个开启加密的时间需要这么长而已, 开启加密后的U盘使用与未加密前的U盘使用是一样的。用户将文件存储到U盘时就会自动完成加密过程,这个过程只是一瞬间而已,相反亦然。
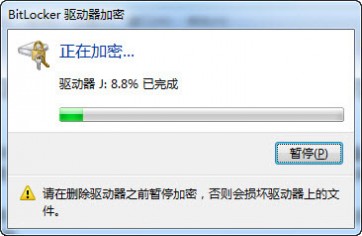
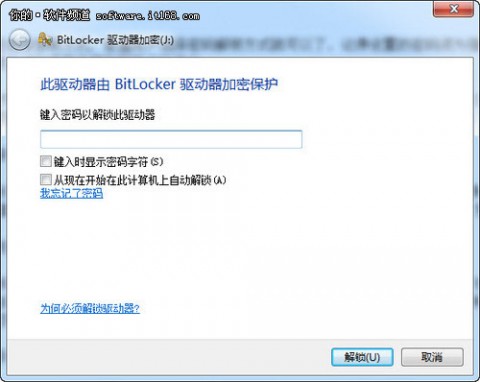
那么,BitLocker加密后的U盘如何使用呢?在Windows7系统下,用户只需要接入加密后的U盘,就会弹出一个解密对话框,输入密码后就可以 解锁该U盘,随后就可以像平时那样使用U盘了。这只是在当前计算机中进行的解锁操作,而不是解密操作,也就是说,解锁后自动在后台完成文件的加密(文件存 储入U盘)及解密(文件从U盘复制到本地)操作。
如果不想每次都输入密码,那就可以勾选“从现在开始在此计算机上自动解锁”选项,以后在本台计算机中插入该加密U盘后就会自动解锁。
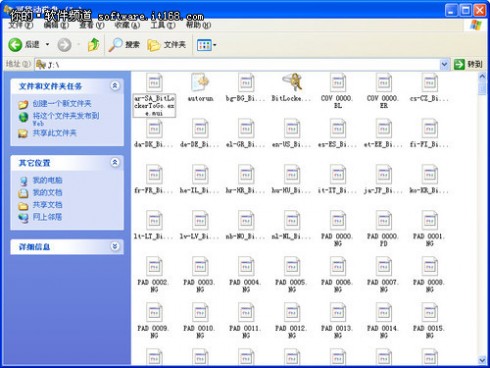
使用 BitLocker 加密的U盘没有解密是无法使用的,就算给别人拿到,没有密码也只能望U盘兴叹,对方能做的只是格式化U盘操作。
BitLocker加密的U盘在Windows XP下打开时,会显示一堆的文件,这时,用户需要找到BitLockerToGo这个可执行文件并运行,就会打开BitLocker To Go阅读器,这个阅读器是微软专门为用户在Windows XP解密BitLocker加密的U盘而设计的,不过需要注意的是,该工具只能帮助用户读取加密的U盘里的文件,而不能修改或添加删除文件。

二 : 用u盘装系统的操作全程图解
为了让用户更好的体验,让大家直观的学会用u启动怎么装系统。下面就为大家简单介绍下用u盘装系统的操作全程图解吧。
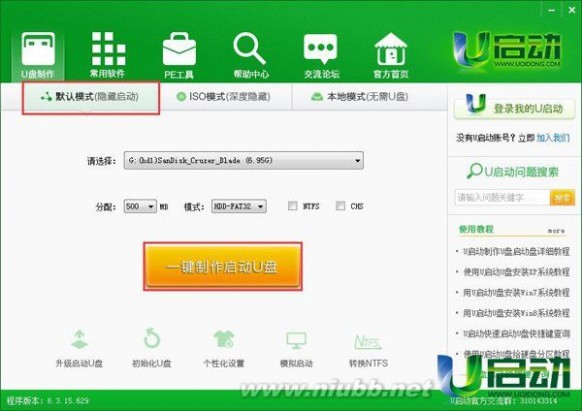
1、准备一个u盘,并制作成u启动u盘启动盘,如下图所示:
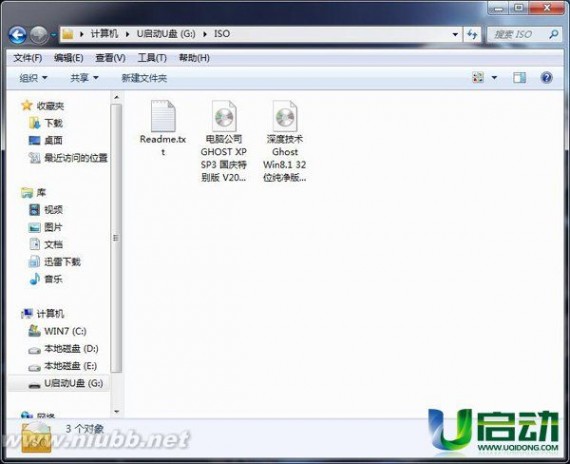
2、将事先下载好的系统镜像文件放入iso文件夹内
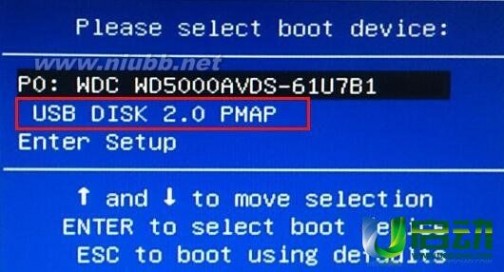
3、重启电脑,开机时按下启动快捷键,进入u启动装机界面
4、选择【02】运行u启动win8pe防蓝屏版,按回车键运行

5、进入u启动win8pe后,系统会自动加载装机工具,我们只需按照提示操作即可

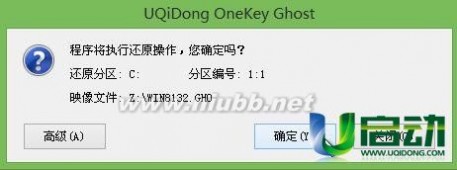
6、耐心等待镜像释放完毕,然后重启完成后续安装
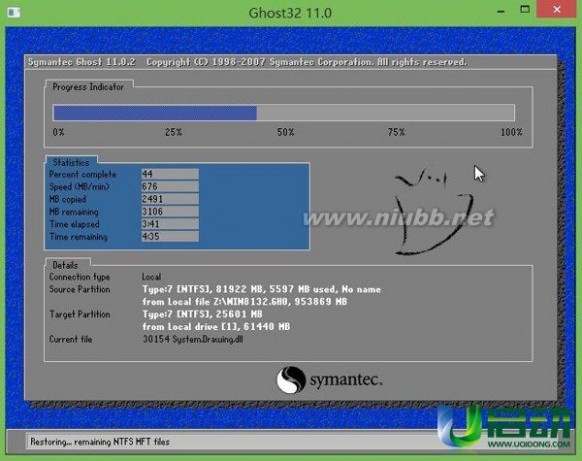
7、重启后电脑自动安装系统,我们只需耐心等待即可
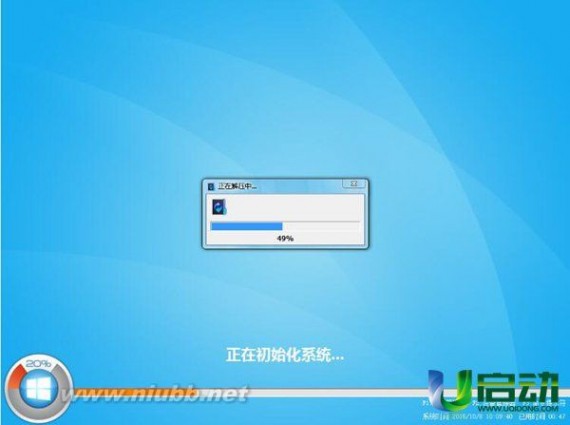
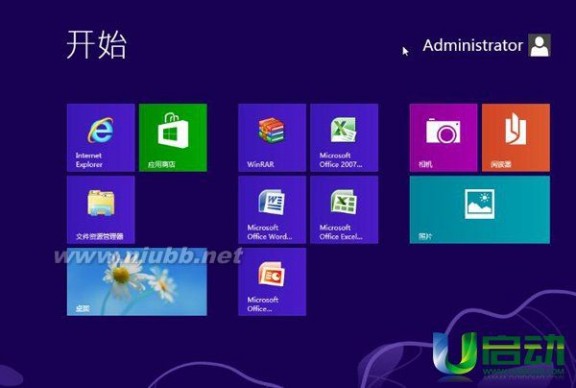
用u盘装系统的操作全程图解就到此结束了,按照上述操作我们就能很轻松的装上新系统了。装系统还用u启动,方便快捷还实用。
三 : 操作系统的IPSECServices解决之01
[修复IPSEC Services]ipsec.reg
在系统中出现:IPSEC Services 服务因下列错误而停止:系统找不到指定的文件。
将以下复制成ipsec.reg后导入。好累啊,不能一次粘贴完!需要的人也辛苦了
Windows Registry Editor Version5.00
[HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows]
[HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\Installer]
"EnableAdminTSRemote"=dword:00000001
[HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\IPSec]
[HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\IPSec\Policy]
[HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\IPSec\Policy\Local]
[HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\IPSec\Policy\Local\ipsecFilter{72385235-70fa-11d1-864c-14a300000000}]
"ClassName"="ipsecFilter"
"description"="匹配该计算机与任何其他计算机之间的所有 ICMP 包。"
"name"="ipsecFilter{72385235-70fa-11d1-864c-14a300000000}"
"ipsecName"="所有 ICMP 通讯量"
"ipsecID"="{72385235-70fa-11d1-864c-14a300000000}"
"ipsecDataType"=dword:00000100
"ipsecData"=hex:b5,20,dc,80,c8,2e,d1,11,a8,9e,00,a0,24,8d,30,21,52,00,00,00,01,\
00,00,00,02,00,00,00,00,00,02,00,00,00,00,00,0a,00,00,00,49,00,43,00,4d,00,\
50,00,00,00,a9,1f,05,9d,22,98,89,4e,84,67,a5,57,19,7d,8e,39,01,00,00,00,00,\
00,00,00,ff,ff,ff,ff,00,00,00,00,00,00,00,00,00,00,00,00,01,00,00,00,00,00,\
00,00,00,00,00,00,00
"whenChanged"=dword:47792928
"ipsecOwnersReference"=hex(7):53,00,4f,00,46,00,54,00,57,00,41,00,52,00,45,00,\
5c,00,50,00,6f,00,6c,00,69,00,63,00,69,00,65,00,73,00,5c,00,4d,00,69,00,63,\
00,72,00,6f,00,73,00,6f,00,66,00,74,00,5c,00,57,00,69,00,6e,00,64,00,6f,00,\
77,00,73,00,5c,00,49,00,50,00,53,00,65,00,63,00,5c,00,50,00,6f,00,6c,00,69,\
00,63,00,79,00,5c,00,4c,00,6f,00,63,00,61,00,6c,00,5c,00,69,00,70,00,73,00,\
65,00,63,00,4e,00,46,00,41,00,7b,00,30,00,33,00,38,00,62,00,39,00,63,00,62,\
00,62,00,2d,00,66,00,39,00,35,00,38,00,2d,00,34,00,37,00,31,00,62,00,2d,00,\
61,00,31,00,64,00,61,00,2d,00,30,00,33,00,63,00,38,00,34,00,66,00,64,00,63,\
00,35,00,31,00,66,00,65,00,7d,00,00,00,53,00,4f,00,46,00,54,00,57,00,41,00,\
52,00,45,00,5c,00,50,00,6f,00,6c,00,69,00,63,00,69,00,65,00,73,00,5c,00,4d,\
00,69,00,63,00,72,00,6f,00,73,00,6f,00,66,00,74,00,5c,00,57,00,69,00,6e,00,\
64,00,6f,00,77,00,73,00,5c,00,49,00,50,00,53,00,65,00,63,00,5c,00,50,00,6f,\
00,6c,00,69,00,63,00,79,00,5c,00,4c,00,6f,00,63,00,61,00,6c,00,5c,00,69,00,\
70,00,73,00,65,00,63,00,4e,00,46,00,41,00,7b,00,64,00,61,00,34,00,31,00,64,\
00,33,00,38,00,62,00,2d,00,33,00,38,00,61,00,65,00,2d,00,34,00,31,00,62,00,\
39,00,2d,00,39,00,34,00,30,00,36,00,2d,00,62,00,65,00,62,00,30,00,30,00,64,\
00,33,00,61,00,64,00,37,00,39,00,63,00,7d,00,00,00,00,00
[HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\IPSec\Policy\Local\ipsecFilter{7238523a-70fa-11d1-864c-14a300000000}]
"ClassName"="ipsecFilter"
"description"="匹配该计算机到任何其他计算机之间的所有 ICMP 包,除了广播、多播、Kerberos、RSVP 和ISAKMP (IKE)。"
"name"="ipsecFilter{7238523a-70fa-11d1-864c-14a300000000}"
"ipsecName"="所有 IP 通讯量"
"ipsecID"="{7238523a-70fa-11d1-864c-14a300000000}"
"ipsecDataType"=dword:00000100
"ipsecData"=hex:b5,20,dc,80,c8,2e,d1,11,a8,9e,00,a0,24,8d,30,21,4a,00,00,00,01,\
00,00,00,02,00,00,00,00,00,02,00,00,00,00,00,02,00,00,00,00,00,55,5b,1b,8a,\
44,82,f1,4a,84,8f,47,ee,f9,49,eb,5a,01,00,00,00,00,00,00,00,ff,ff,ff,ff,00,\
00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00
"whenChanged"=dword:47792928
"ipsecOwnersReference"=hex(7):53,00,4f,00,46,00,54,00,57,00,41,00,52,00,45,00,\
5c,00,50,00,6f,00,6c,00,69,00,63,00,69,00,65,00,73,00,5c,00,4d,00,69,00,63,\
00,72,00,6f,00,73,00,(www.61k.com)6f,00,66,00,74,00,5c,00,57,00,69,00,6e,00,64,00,6f,00,\
77,00,73,00,5c,00,49,00,50,00,53,00,65,00,63,00,5c,00,50,00,6f,00,6c,00,69,\
00,63,00,79,00,5c,00,4c,00,6f,00,63,00,61,00,6c,00,5c,00,69,00,70,00,73,00,\
65,00,63,00,4e,00,46,00,41,00,7b,00,31,00,66,00,33,00,36,00,65,00,33,00,32,\
00,66,00,2d,00,39,00,31,00,65,00,38,00,2d,00,34,00,62,00,65,00,39,00,2d,00,\
62,00,61,00,66,00,39,00,2d,00,31,00,36,00,64,00,30,00,31,00,63,00,62,00,33,\
00,32,00,65,00,33,00,33,00,7d,00,00,00,53,00,4f,00,46,00,54,00,57,00,41,00,\
52,00,45,00,5c,00,50,00,6f,00,6c,00,69,00,63,00,69,00,65,00,73,00,5c,00,4d,\
00,69,00,63,00,72,00,6f,00,73,00,6f,00,66,00,74,00,5c,00,57,00,69,00,6e,00,\
64,00,6f,00,77,00,73,00,5c,00,49,00,50,00,53,00,65,00,63,00,5c,00,50,00,6f,\
00,6c,00,69,00,63,00,79,00,5c,00,4c,00,6f,00,63,00,61,00,6c,00,5c,00,69,00,\
70,00,73,00,65,00,63,00,4e,00,46,00,41,00,7b,00,62,00,65,00,36,00,35,00,39,\
00,62,00,38,00,38,00,2d,00,64,00,37,00,63,00,66,00,2d,00,34,00,65,00,36,00,\
63,00,2d,00,61,00,64,00,33,00,64,00,2d,00,34,00,65,00,63,00,30,00,36,00,30,\
00,61,00,30,00,35,00,33,00,65,00,39,00,7d,00,00,00,00,00
[HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\IPSec\Policy\Local\ipsecISAKMPPolicy{72385231-70fa-11d1-864c-14a300000000}]
"ClassName"="ipsecISAKMPPolicy"
"name"="ipsecISAKMPPolicy{72385231-70fa-11d1-864c-14a300000000}"
"ipsecID"="{72385231-70fa-11d1-864c-14a300000000}"
"ipsecDataType"=dword:00000100
"ipsecData"=hex:b8,20,dc,80,c8,2e,d1,11,a8,9e,00,a0,24,8d,30,21,40,01,00,00,00,\
00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,\
00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,\
00,00,00,00,00,00,00,00,00,04,00,00,00,00,00,00,00,03,00,00,00,00,00,00,00,\
00,00,00,00,02,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,\
00,00,00,00,00,00,00,02,00,00,00,00,00,00,00,00,00,00,00,80,70,00,00,00,00,\
00,00,00,00,00,00,03,00,00,00,00,00,00,00,00,00,00,00,01,00,00,00,00,00,00,\
00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,02,00,00,00,\
00,00,00,00,00,00,00,00,80,70,00,00,00,00,00,00,00,00,00,00,01,00,00,00,00,\
00,00,00,00,00,00,00,02,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,\
00,00,00,00,00,00,00,00,00,00,01,00,00,00,00,00,00,00,00,00,00,00,80,70,00,\
00,00,00,00,00,00,00,00,00,01,00,00,00,00,00,00,00,00,00,00,00,01,00,00,00,\
00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,01,\
00,00,00,00,00,00,00,00,00,00,00,80,70,00,00,00,00,00,00,00
"whenChanged"=dword:47792928
"ipsecOwnersReference"=hex(7):53,00,4f,00,46,00,54,00,57,00,41,00,52,00,45,00,\
5c,00,50,00,6f,00,6c,00,69,00,63,00,69,00,65,00,73,00,5c,00,4d,00,69,00,63,\
00,72,00,6f,00,73,00,6f,00,66,00,74,00,5c,00,57,00,69,00,6e,00,64,00,6f,00,\
77,00,73,00,5c,00,49,00,50,00,53,00,65,00,63,00,5c,00,50,00,6f,00,6c,00,69,\
00,63,00,79,00,5c,00,4c,00,6f,00,63,00,61,00,6c,00,5c,00,69,00,70,00,73,00,\
65,00,63,00,50,00,6f,00,6c,00,69,00,63,00,79,00,7b,00,37,00,32,00,33,00,38,\
00,35,00,32,00,33,00,30,00,2d,00,37,00,30,00,66,00,61,00,2d,00,31,00,31,00,\
64,00,31,00,2d,00,38,00,36,00,34,00,63,00,2d,00,31,00,34,00,61,00,33,00,30,\
00,30,00,30,00,30,00,30,00,30,00,30,00,30,00,7d,00,00,00,00,00
[HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\IPSec\Policy\Local\ipsecISAKMPPolicy{72385234-70fa-11d1-864c-14a300000000}]
"ClassName"="ipsecISAKMPPolicy"
"name"="ipsecISAKMPPolicy{72385234-70fa-11d1-864c-14a300000000}"
"ipsecID"="{72385234-70fa-11d1-864c-14a300000000}"
"ipsecDataType"=dword:00000100
"ipsecData"=hex:b8,20,dc,80,c8,2e,d1,11,a8,9e,00,a0,24,8d,30,21,40,01,00,00,00,\
00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,\
00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,\
00,00,00,00,00,00,00,00,00,04,00,00,00,00,00,00,00,03,00,00,00,00,00,00,00,\
00,00,00,00,02,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,\
00,00,00,00,00,00,00,02,00,00,00,00,00,00,00,00,00,00,00,80,70,00,00,00,00,\
00,00,00,00,00,00,03,00,00,00,00,00,00,00,00,00,00,00,01,00,00,00,00,00,00,\
00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,02,00,00,00,\
00,00,00,00,00,00,00,00,80,70,00,00,00,00,00,00,00,00,00,00,01,00,00,00,00,\
00,00,00,00,00,00,00,02,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,\
00,00,00,00,00,00,00,00,00,00,01,00,00,00,00,00,00,00,00,00,00,00,80,70,00,\
00,00,00,00,00,00,00,00,00,01,00,00,00,00,00,00,00,00,00,00,00,01,00,00,00,\
00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,01,\
00,00,00,00,00,00,00,00,00,00,00,80,70,00,00,00,00,00,00,00
"whenChanged"=dword:47792928
[HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\IPSec\Policy\Local\ipsecISAKMPPolicy{72385237-70fa-11d1-864c-14a300000000}]
"ClassName"="ipsecISAKMPPolicy"
"name"="ipsecISAKMPPolicy{72385237-70fa-11d1-864c-14a300000000}"
"ipsecID"="{72385237-70fa-11d1-864c-14a300000000}"
"ipsecDataType"=dword:00000100
"ipsecData"=hex:b8,20,dc,80,c8,2e,d1,11,a8,9e,00,a0,24,8d,30,21,40,01,00,00,00,\
00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,\
00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,\
00,00,00,00,00,00,00,00,00,04,00,00,00,00,00,00,00,03,00,00,00,00,00,00,00,\
00,00,00,00,02,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,\
00,00,00,00,00,00,00,02,00,00,00,00,00,00,00,00,00,00,00,80,70,00,00,00,00,\
00,00,00,00,00,00,03,00,00,00,00,00,00,00,00,00,00,00,01,00,00,00,00,00,00,\
00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,02,00,00,00,\
00,00,00,00,00,00,00,00,80,70,00,00,00,00,00,00,00,00,00,00,01,00,00,00,00,\
00,00,00,00,00,00,00,02,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,\
00,00,00,00,00,00,00,00,00,00,01,00,00,00,00,00,00,00,00,00,00,00,80,70,00,\
00,00,00,00,00,00,00,00,00,01,00,00,00,00,00,00,00,00,00,00,00,01,00,00,00,\
00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,01,\
00,00,00,00,00,00,00,00,00,00,00,80,70,00,00,00,00,00,00,00
"whenChanged"=dword:47792928
"ipsecOwnersReference"=hex(7):53,00,4f,00,46,00,54,00,57,00,41,00,52,00,45,00,\
5c,00,50,00,6f,00,6c,00,69,00,63,00,69,00,65,00,73,00,5c,00,4d,00,69,00,63,\
00,72,00,6f,00,73,00,6f,00,66,00,74,00,5c,00,57,00,69,00,6e,00,64,00,6f,00,\
77,00,73,00,5c,00,49,00,50,00,53,00,65,00,63,00,5c,00,50,00,6f,00,6c,00,69,\
00,63,00,79,00,5c,00,4c,00,6f,00,63,00,61,00,6c,00,5c,00,69,00,70,00,73,00,\
65,00,63,00,50,00,6f,00,6c,00,69,00,63,00,79,00,7b,00,37,00,32,00,33,00,38,\
00,35,00,32,00,33,00,36,00,2d,00,37,00,30,00,66,00,61,00,2d,00,31,00,31,00,\
64,00,31,00,2d,00,38,00,36,00,34,00,63,00,2d,00,31,00,34,00,61,00,33,00,30,\
00,30,00,30,00,30,00,30,00,30,00,30,00,30,00,7d,00,00,00,00,00
[HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\IPSec\Policy\Local\ipsecISAKMPPolicy{7238523d-70fa-11d1-864c-14a300000000}]
"ClassName"="ipsecISAKMPPolicy"
"name"="ipsecISAKMPPolicy{7238523d-70fa-11d1-864c-14a300000000}"
"ipsecID"="{7238523d-70fa-11d1-864c-14a300000000}"
"ipsecDataType"=dword:00000100
"ipsecData"=hex:b8,20,dc,80,c8,2e,d1,11,a8,9e,00,a0,24,8d,30,21,40,01,00,00,00,\
00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,\
00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,\
00,00,00,00,00,00,00,00,00,04,00,00,00,00,00,00,00,03,00,00,00,00,00,00,00,\
00,00,00,00,02,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,\
00,00,00,00,00,00,00,02,00,00,00,00,00,00,00,00,00,00,00,80,70,00,00,00,00,\
00,00,00,00,00,00,03,00,00,00,00,00,00,00,00,00,00,00,01,00,00,00,00,00,00,\
00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,02,00,00,00,\
00,00,00,00,00,00,00,00,80,70,00,00,00,00,00,00,00,00,00,00,01,00,00,00,00,\
00,00,00,00,00,00,00,02,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,\
00,00,00,00,00,00,00,00,00,00,01,00,00,00,00,00,00,00,00,00,00,00,80,70,00,\
00,00,00,00,00,00,00,00,00,01,00,00,00,00,00,00,00,00,00,00,00,01,00,00,00,\
00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,01,\
00,00,00,00,00,00,00,00,00,00,00,80,70,00,00,00,00,00,00,00
"whenChanged"=dword:47792928
"ipsecOwnersReference"=hex(7):53,00,4f,00,46,00,54,00,57,00,41,00,52,00,45,00,\
5c,00,50,00,6f,00,6c,00,69,00,63,00,69,00,65,00,73,00,5c,00,4d,00,69,00,63,\
00,72,00,6f,00,73,00,6f,00,66,00,74,00,5c,00,57,00,69,00,6e,00,64,00,6f,00,\
77,00,73,00,5c,00,49,00,50,00,53,00,65,00,63,00,5c,00,50,00,6f,00,6c,00,69,\
00,63,00,79,00,5c,00,4c,00,6f,00,63,00,61,00,6c,00,5c,00,69,00,70,00,73,00,\
65,00,63,00,50,00,6f,00,6c,00,69,00,63,00,79,00,7b,00,37,00,32,00,33,00,38,\
00,35,00,32,00,33,00,63,00,2d,00,37,00,30,00,66,00,61,00,2d,00,31,00,31,00,\
64,00,31,00,2d,00,38,00,36,00,34,00,63,00,2d,00,31,00,34,00,61,00,33,00,30,\
00,30,00,30,00,30,00,30,00,30,00,30,00,30,00,7d,00,00,00,00,00
[HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\IPSec\Policy\Local\ipsecNegotiationPolicy{72385233-70fa-11d1-864c-14a300000000}]
"ClassName"="ipsecNegotiationPolicy"
"description"="接受不安全的通讯,但是请求客户端建立信任和安全措施。如果不被信任的客户端不响应请求则使用不安全通讯。"
"name"="ipsecNegotiationPolicy{72385233-70fa-11d1-864c-14a300000000}"
"ipsecName"="请求安全 (可选)"
"ipsecID"="{72385233-70fa-11d1-864c-14a300000000}"
"ipsecNegotiationPolicyAction"="{3f91a81a-7647-11d1-864d-d46a00000000}"
"ipsecNegotiationPolicyType"="{62f49e10-6c37-11d1-864c-14a300000000}"
"ipsecDataType"=dword:00000100
"ipsecData"=hex:b9,20,dc,80,c8,2e,d1,11,a8,9e,00,a0,24,8d,30,21,94,01,00,00,05,\
00,00,00,84,03,00,00,a0,86,01,00,00,00,00,00,00,00,00,00,01,00,00,00,03,00,\
00,00,02,00,00,00,02,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,\
00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,\
00,00,00,00,00,00,00,00,84,03,00,00,a0,86,01,00,00,00,00,00,00,00,00,00,01,\
00,00,00,01,00,00,00,02,00,00,00,02,00,00,00,00,00,00,00,00,00,00,00,00,00,\
00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,\
00,00,00,00,00,00,00,00,00,00,00,00,00,2c,01,00,00,a0,86,01,00,00,00,00,00,\
00,00,00,00,01,00,00,00,02,00,00,00,00,00,00,00,01,00,00,00,00,00,00,00,00,\
00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,\
00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,2c,01,00,00,a0,86,01,\
00,00,00,00,00,00,00,00,00,01,00,00,00,01,00,00,00,00,00,00,00,01,00,00,00,\
00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,\
00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,\
00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,\
00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,\
00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,\
00,00,00,00
"whenChanged"=dword:47792928
"ipsecOwnersReference"=hex(7):53,00,4f,00,46,00,54,00,57,00,41,00,52,00,45,00,\
5c,00,50,00,6f,00,6c,00,69,00,63,00,69,00,65,00,73,00,5c,00,4d,00,69,00,63,\
00,72,00,6f,00,73,00,6f,00,66,00,74,00,5c,00,57,00,69,00,6e,00,64,00,6f,00,\
77,00,73,00,5c,00,49,00,50,00,53,00,65,00,63,00,5c,00,50,00,6f,00,6c,00,69,\
00,63,00,79,00,5c,00,4c,00,6f,00,63,00,61,00,6c,00,5c,00,69,00,70,00,73,00,\
65,00,63,00,4e,00,46,00,41,00,7b,00,62,00,65,00,36,00,35,00,39,00,62,00,38,\
00,38,00,2d,00,64,00,37,00,63,00,66,00,2d,00,34,00,65,00,36,00,63,00,2d,00,\
61,00,64,00,33,00,64,00,2d,00,34,00,65,00,63,00,30,00,36,00,30,00,61,00,30,\
00,35,00,33,00,65,00,39,00,7d,00,00,00,00,00
[HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\IPSec\Policy\Local\ipsecNegotiationPolicy{7238523b-70fa-11d1-864c-14a300000000}]
"ClassName"="ipsecNegotiationPolicy"
"description"="允许不安全的 IP 包经过。"
"name"="ipsecNegotiationPolicy{7238523b-70fa-11d1-864c-14a300000000}"
"ipsecName"="许可"
"ipsecID"="{7238523b-70fa-11d1-864c-14a300000000}"
"ipsecNegotiationPolicyAction"="{8a171dd2-77e3-11d1-8659-a04f00000000}"
"ipsecNegotiationPolicyType"="{62f49e10-6c37-11d1-864c-14a300000000}"
"ipsecDataType"=dword:00000100
"ipsecData"=hex:b9,20,dc,80,c8,2e,d1,11,a8,9e,00,a0,24,8d,30,21,04,00,00,00,00,\
00,00,00,00
"whenChanged"=dword:47792928
"ipsecOwnersReference"=hex(7):53,00,4f,00,46,00,54,00,57,00,41,00,52,00,45,00,\
5c,00,50,00,6f,00,6c,00,69,00,63,00,69,00,65,00,73,00,5c,00,4d,00,69,00,63,\
00,72,00,6f,00,73,00,6f,00,66,00,74,00,5c,00,57,00,69,00,6e,00,64,00,6f,00,\
77,00,73,00,5c,00,49,00,50,00,53,00,65,00,63,00,5c,00,50,00,6f,00,6c,00,69,\
00,63,00,79,00,5c,00,4c,00,6f,00,63,00,61,00,6c,00,5c,00,69,00,70,00,73,00,\
65,00,63,00,4e,00,46,00,41,00,7b,00,30,00,33,00,38,00,62,00,39,00,63,00,62,\
00,62,00,2d,00,66,00,39,00,35,00,38,00,2d,00,34,00,37,00,31,00,62,00,2d,00,\
61,00,31,00,64,00,61,00,2d,00,30,00,33,00,63,00,38,00,34,00,66,00,64,00,63,\
00,35,00,31,00,66,00,65,00,7d,00,00,00,53,00,4f,00,46,00,54,00,57,00,41,00,\
52,00,45,00,5c,00,50,00,6f,00,6c,00,69,00,63,00,69,00,65,00,73,00,5c,00,4d,\
00,69,00,63,00,72,00,6f,00,73,00,6f,00,66,00,74,00,5c,00,57,00,69,00,6e,00,\
64,00,6f,00,77,00,73,00,5c,00,49,00,50,00,53,00,65,00,63,00,5c,00,50,00,6f,\
00,6c,00,69,00,63,00,79,00,5c,00,4c,00,6f,00,63,00,61,00,6c,00,5c,00,69,00,\
70,00,73,00,65,00,63,00,4e,00,46,00,41,00,7b,00,64,00,61,00,34,00,31,00,64,\
00,33,00,38,00,62,00,2d,00,33,00,38,00,61,00,65,00,2d,00,34,00,31,00,62,00,\
39,00,2d,00,39,00,34,00,30,00,36,00,2d,00,62,00,65,00,62,00,30,00,30,00,64,\
00,33,00,61,00,64,00,37,00,39,00,63,00,7d,00,00,00,00,00
四 : 解析UML9种图的作用
本文和大家重点讨论一下UML9种图的概念,UML中有五类图,共有9种图形,每种图形都有各自的特点,下面就让我们一起来看一下这些图形特点的详细介绍吧。
UML9种图简介
1、用例图
说明的是谁要使用系统以及使用该系统可以做些什么。UML9种图中一个用例图包含了多个模型元素,如系统、参与者和用例,并且显示了这些元素之间的各种关系,如泛化、关联和依赖。
2、活动图
UML9种图中活动图能够演示出系统中哪些地方存在功能,以及这些功能和系统中其他组件的功能如何共同满足前面使用用例图建模的商务需求。
3、状态图
可以捕获对象、子系统和系统的生命周期。它们可以告知一个对象可以拥有的状态,并且事件(如消息的接收,时间的流逝、错误、条件为真等)会怎样随着时间的推移来影响这些状态。一个状态图应该连接到所有具有清晰的可标志状态和复杂行为的类;该图可以确定类的行为以及该行为如何根据当前的状态而变化,也可以展示哪些事件将会改变类的对象的状态。
4、顺序图
也叫做序列图是用来显示参与者如何以一系列顺序的步骤与系统的对象交互的模型。UML9种图中顺序图可以用来展示对象之间是如何进行交互的。顺序图将显示的重点放在消息序列上,即消息是如何在对象之间被发送和接收的。
5、类图
能够让我们在正确编写代码以前对系统有一个全面的认识。UML9种图中类图是一种模型类型,确切的说,是一种静态模型类型。一个类图根据系统中的类以及各个类之间的关系描述系统的静态视图。
6、对象图
与类图极为相似,只是它描述的不是类之间的关系。
7、协作图
可以看成类图和顺序图的交集,协作图建模对象或者角色,以及它们彼此的通信方式。
8、组件图
UML9种图中组件图用来建模软件的组织以及其相互之间的关系。这些图由组件标记符和组件之间的关系构成。在组件图中,组件是软件的单个组成部分,它可以是一个文件、产品、可执行文件和脚本等。
9、部署图
用来建模系统的物理部署。例如计算机和设备,以及它们之间是如何连接的。部署图的使用者是开发人员、系统集成人员和测试人员。
五 : U盘装系统操作步骤图解
U盘装系统操作步骤图解
相信有的朋友去电脑城组装电脑的时候,会看见装机人员安装系统不再需要光驱,而插入U盘安装系统,U盘安装系统方便了许多,电脑光驱容易坏,使用寿命短,一般老电脑的光驱都不怎么好使,而U盘就不需要光驱就能安装,只要有完好的USB接口就行,U盘就是携带也方便许多,U盘的体积比系统安装光盘小得多。
接下来为大家提供两个我在网上精心搜集的U盘安装系统教程。
第一个教程我是亲自验证过的,我现在使用的系统安装U盘都还是按照这个教程制作的,很好用的。另外我给教程内容完善了一下,比网上流传的更加详细而通俗易懂。如果通过这个教程还不能用U盘安装系统成功,再看看最下面我提供的“利用老毛桃WinPE制作启动U盘安装系统视频教程 ”。
第二个教程我看了一下应该是没问题的,大家试一下就清楚了,教程一点也不复杂,自己有个U盘就行,还需要下载个系统的镜像。
本文内容导航:
一、用U盘装系统的操作步骤图解(亲自验证)
二、U盘装系统详细图文教程(XP、win7系统全通用)
三、利用老毛桃WinPE制作启动U盘安装系统视频教程
一、用U盘装系统的操作步骤图解(亲自验证)
装系统前的准备

一个能启动电脑的
U盘和一个操作系统的镜像
在安装系统前,需要准备好一些东西。一个是操作系统的镜像(一般后缀名为.ISO),操作系统的镜像可以从网上下载,或者是从系统安装光盘中提取,一般都是使用快速安装版的Ghost XP系统镜像,另一个就是能启动的U盘。
下面我们就来讲解怎么安装Windows XP系统,其它版本的系统也是一样的操作方法。 注:读懂本文需要了解安装操作系统的一些基础知识。
首先是制作一个能启动电脑的带WindowsPE的启动U盘
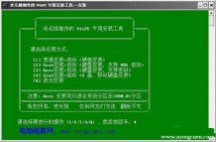
先到网上去下载一个叫“老毛桃WinPE”的工具到硬盘里,再把U盘接在电脑上,然后按下面的步骤一步步来就可以制作一个能启动的U盘了。
老毛桃winpe(U盘启动盘制作) 下载地址:
选第4项,然后回车。
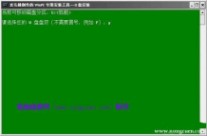
输入U盘的盘符,然后回车
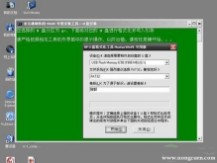
来到格式化步骤,按默认的设置,点“开始”就行

顺利格式化
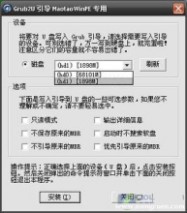
引导部分
这里要说明一下,在“设备”里有两个选项,一个是电脑的硬盘,一个是要制作的U盘。这里一定要选对U盘而别选错硬盘,从大小就能分出来哪个是U盘。笔者的U盘是2G

的,所以应该选择(hd1)[1898M]。下面的“选项”部分可以不用管,默认不勾选任何参数就行。确认好以上步骤后,点“安装”然后进行下一步。
写入引导完毕,按任意键继续
要给启动U盘设个密码
本来笔者不想设置启动U盘的密码,但这个步骤不能跳过,所以没办法只好设了一个密码。设置完后,一定要牢记你设好的密码,否则启动U盘会无法使用。

制作完毕
U盘启动盘制作完成后,再把你准备好的操作系统镜像文件(一般后缀名为.ISO)放到你的U盘里。
当你完成以上步骤后,恭喜,一个具有启动功能的U盘已经来到你的身边。你再也不用心烦没有光驱不能从光驱启动了,因为以后你可以从U盘启动再安装操作系统!想知道怎么操作吗?
把电脑的第一启动项设为USB设备启动
以往用光盘装系统,必须调整启动项为光驱启动,而现在我们要用U盘装系统,所以要调整为U盘启动。关于这个,不同电脑不同版本的bios有不同的设置方法,不过都大同小异,目的就是让电脑的第一启动项变为U盘启动。下面我们举例几个不同bios的调整方法。
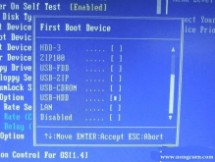
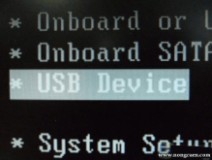
最常见的Phoenix-Award的bios选项,选择USB-HDD即可
dell品牌机的bios调整选项
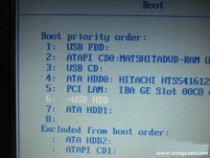

ThinkPad系列笔记本的BIOS
惠普商用系列笔记本的BIOS
可以看到以上的bios选项都各不相同,但是调整的选项都是为了一个目的:把电脑的启动项设为从USB设备启动,这样才能达到从U盘启动电脑的效果。


用能启动的U盘安装XP
先把具备启动功能的U盘接上电脑。
启动电脑
启动电脑后,会要求你输入启动U盘的密码,也就是前文在制作这个启动U盘时设置的密码。当你输入正确的密码后,即可看到一个选择菜单,选择“WinPE By:MAOTAO”。(电脑组装网:www.61k.com提供的U盘装系统教程)

进入WinPE
然后就会进入一个运行在U盘上(不是运行在电脑的硬盘上)的迷你操作系统WinPE,它具备很多类似XP的功能,有了它我们就可以对电脑随心所欲了。
可以对C盘进行格式化
怎么个随心所欲法?能直接对C盘进行格式化操作,这个够震撼了吧?在安装新的XP前,我们先对C盘进行格式化操作,用U盘上的WinPE把电脑里的C盘格式化后,请出WinPE系统自带虚拟光驱来帮忙。

运行在U盘上的WinPE自带了一个虚拟光驱
载入XP系统的镜像
需要载入XP系统的镜像(常用的是快速安装版的Ghost XP系统镜像)一般就是放在U盘里的,当然电脑其它盘里也可以,只是U盘里的系统镜像是自己放的,知根知底,这样也方便安装。
用虚拟光驱载入系统镜像后会多出一个驱动器
我们看到,在用虚拟光驱载入系统镜像后,“我的电脑”目录里多了一个
GHOSTXP-6.5NTFS的驱动器盘符。这就是我们即将要安装的系统所在位置。
启动WinPe的Ghost
接着我们启动另外一个WinPE自带的软件诺顿Ghost。用它来把系统的ghost镜像恢复到之前被格式化的电脑的C盘里。
跟平时使用GHOST的步骤没什么两样

启动GHOST后,使用方法就和通常使用GHOST来恢复系统没什么区别了。先选择From Image,然后找到虚拟光驱载入的光盘目录,把GHOSTXP.GHO选上,接着选要恢复到的硬盘,然后选择要恢复到的分区。
点击YES,等着它恢复完就行
前面都选择好之后,会弹出一个对话框问你是否要将指定的GHO镜像恢复到电脑的C盘去,点击yes就可以。

重启进入系统,重装完毕
当GHOST镜像恢复完毕后,即可重启进入系统。至此,用U盘安装操作系统完毕!你可以忘掉没有光驱无法安装操作系统的烦恼了。值得一提的是,由于整个过程都是在硬盘里读取数据,所以在安装速度上比用光盘安装快很多。如果还有什么不懂的地方可以看看本文最下面的“利用老毛桃WinPE制作启动U盘安装系统视频教程 ”。
其实这只是用U盘安装系统的其中一种方法而已,还有很多其它方式可以安装系统,本文就不再一一举例。也许细心的你已经发现,有了这个启动U盘,就不用再害怕系统崩溃后,重要的资料保存在C盘里而无法挽救了,因为只要你用U盘启动WinPE,就可以进去将重要资料备份到其它分区里。希望网友们可以根据这个举一反三,灵活运用WinPE这个安装在U盘上的非常使用的工具。
二、U盘装系统详细图文教程(XP、win7系统全通用)
几乎可以这样说:任何一个拥有电脑的用户都会有重装系统的需要。对大多数用户来说,用系统盘装系统并不难,难的是光驱坏了怎么装系统,或者电脑没有光驱怎么装系统?没错,那就要用U盘了。其实通过U盘安装操作系统是一种非常简单也很实用的方式,此次我们整理U盘装系统的操作全程图解,详细教大家怎么用U盘装系统。

U盘
在用U盘装windows系统前,需要准备的东西:
1.一台电脑(这是废话#_# ,但是电脑必须有USB插口)
2.完好无损坏的U盘一个(建议不小于4G,当然,拿手机的内存卡插入读卡器充当U盘也是OK的)
3.操作系统的镜像(一般后缀名为.ISO,下载后保存在电脑的硬盘里,不是保存在U盘里!)
4.将U盘插入电脑的USB插口(台式电脑最好插入机箱后面的插口)
第一步:用U盘做系统,制作一个启动U盘。
用U盘装系统首先要制作一个能启动电脑的带WindowsPE的启动U盘
制作启动U盘的软件比较多,这里以UltraISO这款软件为例。
首先,下载UltraISO软件,并安装。
点此下载UltraISO软碟通9.3.6中文版
安装完成之后,注意:右键点图标,选择“以管理员身份运行”!(不要直接双击打开,否则可能造成无法成功写入!)如图1:
运行UltraISO后,依次点击【文件 - 打开】,找到已经下载好的想要写入U盘的系统镜像文件(一般是.ISO格式的),如图2:

打开之后应该是图3这样的:
点击【启动】菜单,选择【写入硬盘镜像】。
执行【写入硬盘映像】后,在下面的【消息】列表中找到你已经插入的U
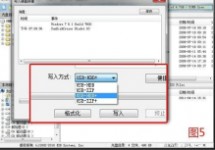
盘,选中它。在【写入方式】一项中有四种模式,选哪个主要取决于你的主板支持的启动类型,可以在刻录前进CMOS看一下,注意有的主板需要插入U盘才会显示支持的类型。一般选择HDD+就可以了,选择完成后,点击【写入】。如图5:
点击【写入】以后,会弹出提示,提示你U盘将会被格式化(如图6),务必提前把U盘里的数据备份。
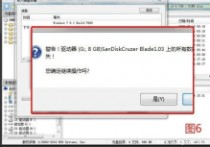

点击是,开始写入。如图7:
写入完成后会显示刻录成功,这时你的U盘功能就相当一个系统安装盘了!可以用它安装系统了!
第二步:使用制作好的U盘安装系统
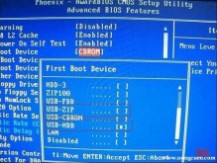
有了一个启动U盘在手了,下面的事情就简单多了,基本和使用光盘装系统没有太大区别。不同电脑不同版本的bios有不同的设置方法,不过都大同小异,目的就是让电脑的第一启动项变为U盘启动。开机之后按屏幕上的提示文字进入BIOS,图片8以最常见的Phoenix-Award的bios选项为例,选择USB-HDD或者USB ZIP即可,具体要看上面写入时你选择的写入方式!和写入方式保持一致即可!上面写入时我们选择的是HDD+模式,所以这里我们选择HDD(注:HDD是Hard Disk的缩写)
设置完第一启动项以后,把写入完成的U盘插入电脑,重启电脑。电脑启动后开始安装windows,和光盘安装没什么区别,安装步骤不再赘述。
三、利用老毛桃WinPE制作启动U盘安装系统视频教程
本文标题:用u盘装系统的操作全程图解-在Windows7中将U盘用BitLocker加密的操作步骤61阅读| 精彩专题| 最新文章| 热门文章| 苏ICP备13036349号-1